Privileged access management or PAM is basically a solution that helps an organization to restrict privileged access within an existing active directory environment by providing secure, control, manage and monitoring all the privileged account access to critical assets.Privileged access management serves the purpose which is it gives the absolute security to any privileged account. PAM takes the credentials of a privileged account user and puts them in a secure repository. By storing the information in the secure repository reduce the probability of these credentials may get stolen.
Privileged account management is generally used for organization security to maintain credentials security. For this reason, this privileged account needs to access sensitive information from the system. It means these accounts face a huge amount of vulnerabilities. Inside and outside attacks are the result of the vulnerabilities. By attacking, the attackers take benefit from the account. Managing the privileged account involves a huge amount of challenges because there’s much more at stake than a simple user account. As the PAM is a complex security system that represents a huge number of difficulties to maintain. This system needs to maintain the balance between security as well as the ease of access with the organization.
The lack of proper Privileged access management causes a series of issues in the company. The first of them is password management. Using the same password for a longer period by the users allows the hackers to hack the password. It is a great threat to the organization. Then comes managing access issues. Any abruption in monitoring and controlling access can result in a huge loss. Without monitoring and auditing, the system remains vulnerable to unauthorized access. Scalability is another problem in this regard. It occurs because of not using automated tools by the company owners. The security processes are not simple and it is a great problem for sure.
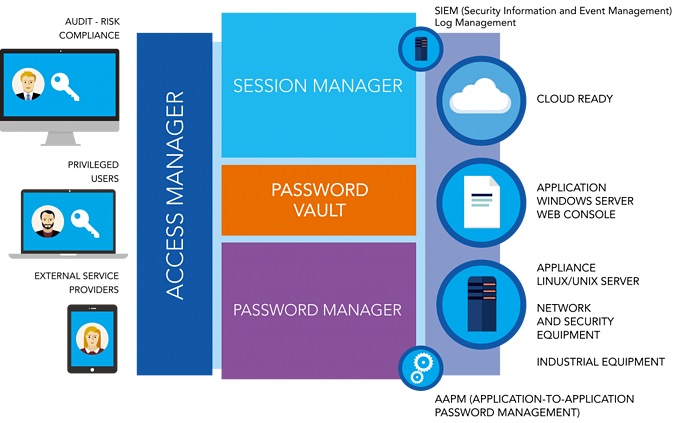
PAM is based on the active directory domain system which is specifically for domain account authentication & authorization. So, it can deal with all the above-mentioned problems. PAM mainly separates the privileged account with the regular account and puts the privileged account in a repository. If the privileged account needs to be used first, it needs to send a request after receiving the request the PAM system follows these procedures. First a multi-factor authentication for administrator which has some specific authentication for the admin level. The access manager maintains the permission of the privileged account. A password vault stores password or gives a one-time password for that cer Read more

Controlling access to your company website by using PAM is a great idea. Bugsbd has developed the best PAM solution for you. Our solution is made to assess the highest benefits for you as a user. Some of the benefits are-
Read more
Our security experts are standing by to help you with an incident or answer questions about consulting services.